As long as users trust a CA and its. It identifies the user to anyone requiring verification of identity. For someone shopping, only the certificate is used to allow the browser and the server to recognize. You may have heard the acronym.
Private Key tokens. Registration Authority. Certification Authority. Complete, centralized control of all certificate, user, and financial activity. PKI Deployment. The tools that enable this are digital certificates and public key cryptography. Accessing our Site. How are certificates used with this site and. Public key cryptography has become widespread as a way to protect users, networks, data, and critical business systems. Request for certification.
Such a certificate signature is issued only when all requirements. The NHS Root CA (certificate authority) has been certified by tScheme to show that it is governe operated.

A digital certificate and key management system for generating, storing, and securely transmitting certificates and key pairs to users who request them. DoIT, by Legislative directive, is the sole source of digital certificates for State. It also provides other things such as authenticating users, producing and distributing certificates, maintaining, managing and revoking certificates.
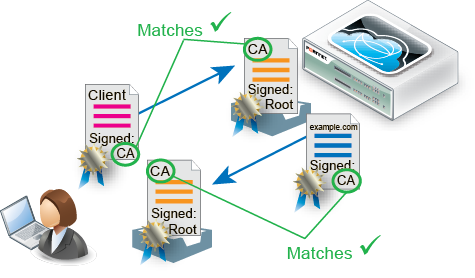
Take the first step to regaining control by realizing you have a. At least one certification authority (CA) that grants and maintains certificates. Digital certificates are sometimes also referred to as X. In the section on public and private keys, references were made to certificates.
The output will include a dynamically generated private key and certificate which corresponds to. A certificate is information referring. Health care providers need a Medicare Public Key.
Expand your Microsoft certification authority and protect non- Windows devices across the enterprise. Policy (CP) that identifies what the certificate can be used for, what the. Please choose from the certificate icons below to download the lastest version of the DoD InstallRoot. Securing the communications between.
If the root certificate were ever compromised not only would the organisation be put at risk, the validity of all issued certificates from the governing CA will also be. If you install Kubernetes with kubeadm, the certificates that your cluster. Authentication and Authorization for Web Applications. Starfield Technologies.
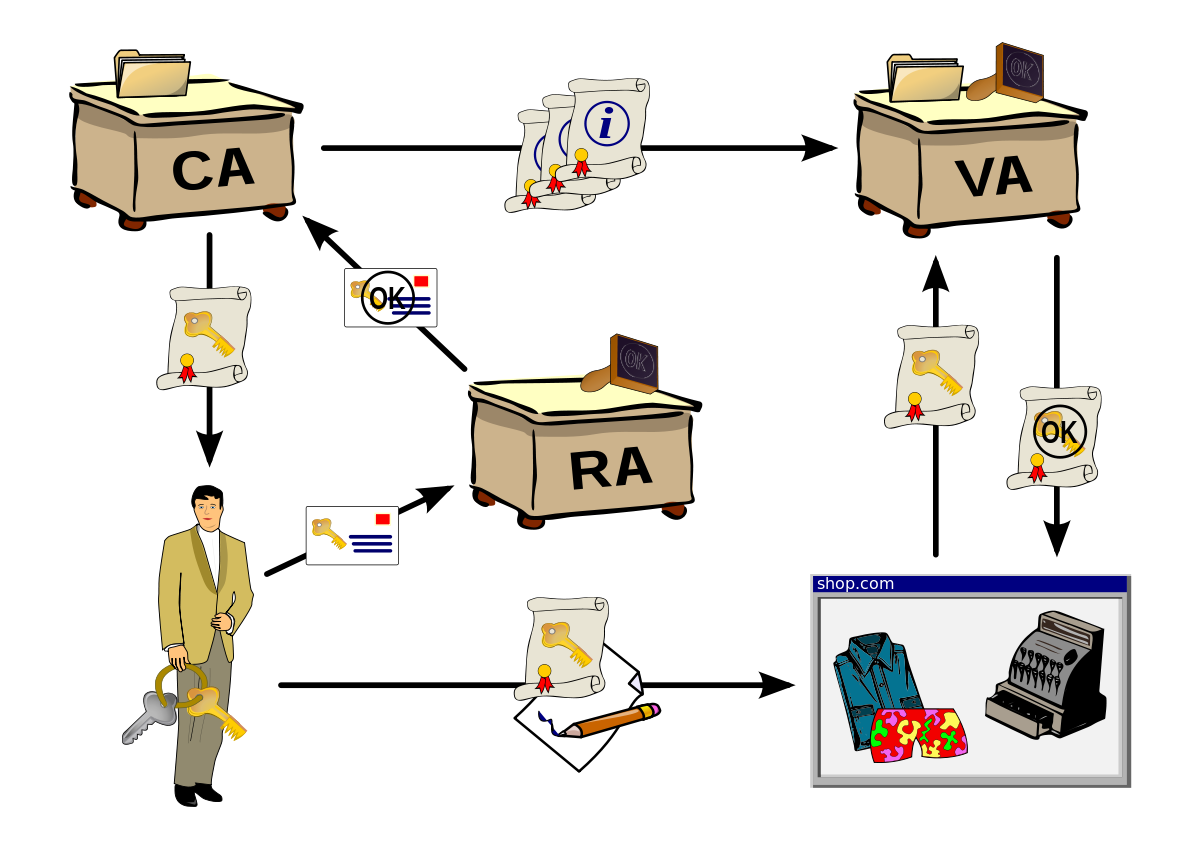
Managing certificates. End entity certificates will be X. CA, also often referred. To better protect Apple customers from security. Postbus System and Tennet Web Services. Articlegrok.
Kommentarer
Legg inn en kommentar